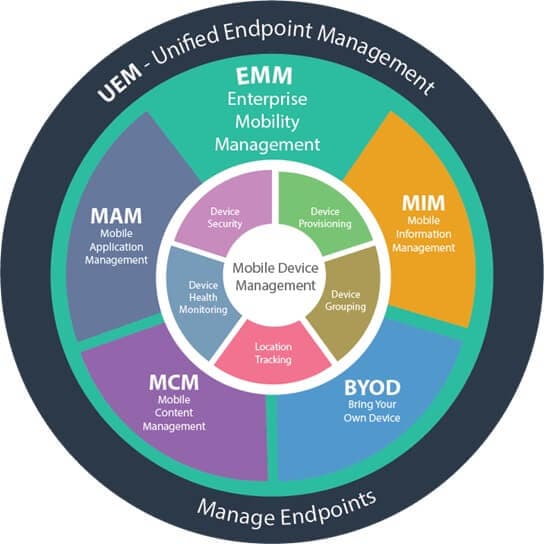
MDM VS. MAM 2024: Which One is Better?
Jul 12, 2024 • Filed to: Latest News & Tactics • Proven solutions
These days Many companies are shifting to remote work, which is only possible through technology like remote conversation and monitoring, virtual classes, and mobile devices to arrange and monitor activities. Also, many companies have moved to a "bring your own device" (BYOD) system because workers want to do their work at home or the office without changing devices.
Mobile Device Management (MDM) and Mobile Application Management (MAM) are the most effective methods to manage all remote data and information conversations through mobile devices. People often think that Mobile Device Management (MDM) and Mobile Application Management (MAM) are the same, but they are not. This article has a comprehensive comparison of both methods.
Detailed Comparison: MDM VS. MAM
Here is a detailed comparison of MDM and MAM:
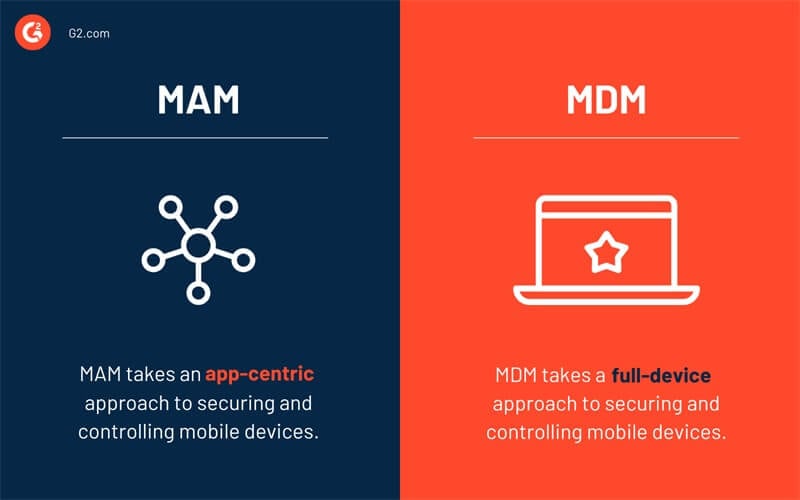
MDM (Mobile Device Management)
MDM allows you to manage all of your devices from one location. You can send commands and profile data to other devices using MDM. The apparatus may be owned by the user or your business and require secure and wireless configuration. MDM solutions can employ a built-in mechanism in both iPhone and Android devices to enable an organization to manage these devices.
MAM (Mobile Application Management)
Mobile Application Management (MAM) enables the management and monitoring of company data on user devices such as iPhones and Android smartphones. With MAM, You can delete data that you no longer want users to access and set up application control policies to stop employees from taking sensitive company data to store it elsewhere.

Similarities between MDM and MAM
MAM and MDM both have features for wrapping apps and putting apps in containers. The Administrator can control, protect, and upgrade apps on company devices by using these methods. Both have some similarities in their features.
- Most EMM or UEM suites include both MAM and MDM. They are often marketed together as a component of a complete plan to manage and protect devices.
- MAM and MDM both have features for wrapping apps and putting apps in containers. The Administrator can control, protect, and upgrade apps on company devices.
- MAM and MDM have authorization and authentication functions for users and groups.
- MAM and MDM can control access and allow users to use third-party products embedded with their own.
- Both can help control, monitor, and enhance your staff's use of the company's digital resources.
Principles to work MDM &MAM
The principles of working with MDM & MAM are the following:
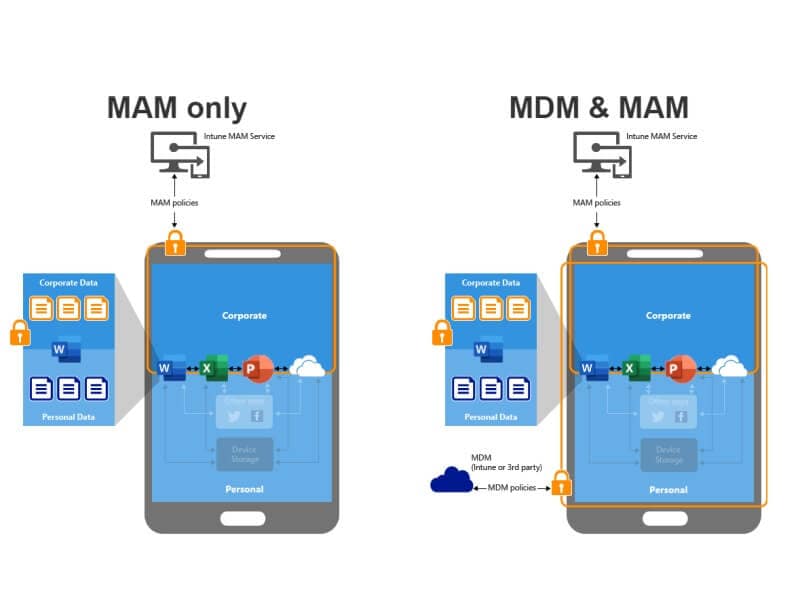
MDM (Mobile Device Management)
1- MDM tries to set up a centralized view for all databases to link all data values. In this way, MDM provides "corporate connectivity to normalize, combine, and create an official source for data from different sources of information.
2- Once the MDM setup is over, it ensures that all the data stays consistent and correct and makes this data available to end users and other applications.
Many organizations prefer MDM for several reasons. Most of the time, it is preferred to improve internal efficiency, business, and workflow.
MAM (Mobile Application Management)
1- Mobile application management (MAM) software controls business apps and data on mobile devices without controlling the entire device.
2- Its tools monitor the life span of business applications that have been installed and stop other non-concerned applications from trying to access company data.
3- MAM software also ensures that business policies are followed and keeps business apps and data separate from personal data on the same mobile device.
MDM Vs. MAM: Application Scenarios
As mentioned earlier, Most EMM or UEM suites include MAM and MDM. They are often offered together as a component of a complete plan to manage and protect devices. MAM is used along with MDM to protect, monitor, and set restrictions on the applications in mobile devices.
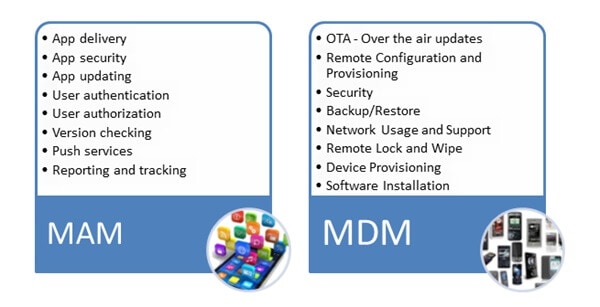
MDM and MAM Application Scenarios
Education
Schools and other environments of education are slowly switching to teaching methods that use tablets to make the learning and teaching process more accessible. However, before they can work to educate, tablets and laptops must be set up correctly and have all the necessary applications installed.
MDM and MAM can set up the whole fleet of devices and limit how they can be used, like blocking killer apps or blocking access to specific websites.

Small Businesses
Small and medium-sized businesses can do a lot with cloud-based MDM. It can help small and medium-sized companies keep a record of their devices and manage them from a central location without hiring an IT expert. Working devices through a single platform can save time and make it easier to avoid security issues.

Sales and serving Sector
MDM software can change any mobile device to function in a way that fits your business and services. As you know, mobiles and tablets frequently run in the sales and serving industries. You can use them as cash registers, information displays, and self-checkout kiosks.
In restaurants, tablets aim to order food or look at a seating map. A device with more than one user can be used safely by putting it in Single-App Tablet mode or other restrictions.

Company Data Protection
With MAM, administrators can make sure that mobile apps follow company policy. So, the admin can control how business data is shared between apps and ensure privacy concerns are encountered. It also allows you to keep work applications and services separate from your data on the same device.

MDM and MAM Popularity
Both components of a complete plan are for managing and protecting mobile devices. MDM and MAM solutions give IT administrators a complete view of their network's current assets, including command over device security policies and application management. Having more control over company data on devices protects the company's privacy and keeps data secure.
MDM solutions can turn employees more productive and allow them to use their devices while keeping the network safe. MDM and MAM are flexible and easy to set up and operate. It is easy to control multiple devices from a single login screen. This makes it a simple and quick solution for everyone.
That's why MDM and MAM are prevalent ways to protect and make data consistent, improving an organization's work efficiency and workflow.
Pros and Cons of MDM and MAM
Following are some pros and cons of MDM and MAM.
MDM Pros & Cons
Pros of MDM
Remote management of devices and Users
Remote management is the key benefit of the MDM. Suppose a company's employees use several mobile devices to perform daily tasks. In that case, it can be challenging to monitor the activities of all the devices and establish a comprehensive security mechanism for those devices.
With the MDM solution, it is easy to keep an eye on what users are doing and ensure that none of the employees can get content on their devices that is not allowed. And you can retain all the devices securely by putting the proper security mechanism on them.
Data Backup
MDM can back up essential data from the devices automatically. You can automatically set up all the devices in your network to back up their data to the central server. So, even if one device gets lost or stops working, you will not have to worry about losing any data. You can quickly get all the essential files back from the backup and keep your company running.
Cost Effectiveness
MDM solution is cost-effective for your business. You can implement a BYOD policy along with an MDM solution for more cost-effectiveness. This way, you would only have to spend a few bucks buying cell phones for your company. You will also add a dedicated security system, so you won't have to worry about data theft or other security issues.
Security
While implementing the BYOD policy, data security, network, and information risks are increased. But MDM makes it easier to protect sensitive data from getting stolen. You can grant the users limited access to the network and change app permissions so that no unauthorized third-party apps can access sensitive information about your company.
Cons of MDM
Audit Reports
It is vital to do regular security audits and make specific reports. But, security auditing takes a lot of time and requires many people.
Limited Visibility
Most MDMs only give a few critical pieces of information about a device. As a result, administrators must write and run custom commands to collect valuable data and respond to essential questions about the fleet.
MAM Pros & Cons
Following are some pros and cons of MDM and MAM.

Pros of MAM
Customized app Catalog
Mobile Application Management makes it possible for businesses to make app collections specific to their needs. IT admins of organizations can install different kinds of public or in-house enterprise apps for their end users or install some selective apps on the device.
Scheduling app updates
App management is more than just distributing and installing apps across the company. IT admins of companies can also keep apps of all the connected devices up to date. So that the devices can work at their best and cyber risks are kept to a minimum. IT admins can keep track of the different versions of apps and schedule updates with the help of Mobile Application Management solutions.
Efficiency improvements
MAM allows the IT administrator to manage, supervise, secure, distribute, update, and delete enterprise apps and optimize several routine activities, all done from a central location. Moreover, employees can be more productive because they can use company apps on their corporate or personal devices, no matter where they are.
Security Improvements
If you have adopted a BYOD policy, MAM keeps company apps safe and separate from private apps and unauthorized access. It stops any data transmission or information sharing from occurring. In short, it keeps company apps and the sensitive company data they store safe from potential threats, misuse, and risks.
Cons of MAM
Costly
When MAM is used, the costs of making, supporting, and distributing applications go up. Costs can go up because implementing the Software development kit takes more development time, users or devices need more licenses, and the IT admin needs more time to manage the MAM platform.
Which One is Better for Me?
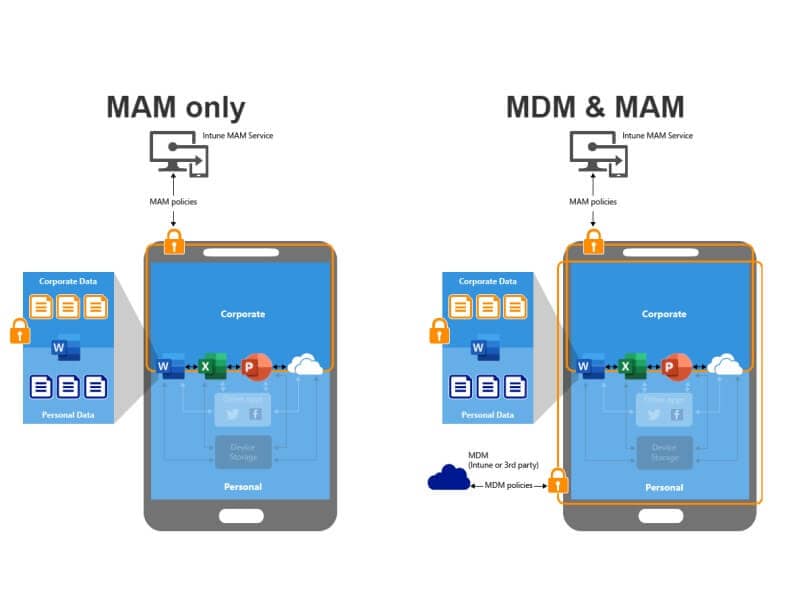
Mobile Device Management (MDM) and Mobile Application Management (MAM) are often thought to be the same thing. MDM is a way of protecting and controlling mobile devices like smartphones and tablets.
In contrast, MAM protects the apps on those devices that are used to access organizational data, like Outlook, SharePoint, and OneDrive. MDM software is often made to work with more than one operating system, like iOS and Android. It keeps a profile of each device, which lets companies remotely track, lock, secure, encrypt, and wipe them as needed.
Mobile Application Management doesn't change how the device works, but it makes software applications more secure and easier to install. IT admins can use MAM to pre-configure business apps, push them to a fleet of devices, do regular maintenance and updates, install and remove apps from devices, and do much more.
So, both are important to manage and protect the devices.
Conclusion
Mobile Device Management (MDM) and Mobile Application Management (MAM) have similarities but different approaches. MDM is a way of protecting and controlling mobile devices like smartphones and tablets through a single location, while MAM protects the apps on those devices that are used to access organizational data. Both tools are important for managing, organizing, and protecting the devices and circulated data of the company.
iPhone Unlock
- Access Locked iPhone
- 1. Reset Locked iPhone Without iTunes
- 2. Erase Locked iPhone
- 3. Get Into Locked iPhone
- 4. Factory Reset Locked iPhone
- 5. Reset Locked iPhone
- 6. iPhone Is Disabled
- 7. Fix iPhone Unavailable Issue
- 8. Forgot Locked Notes Password
- 9. Unlock Total Wireless Phone
- 10. Review of doctorSIM Unlock
- iPhone Lock Screen
- 1. Unlock iPhone with Apple Watch
- 2. Unlock Forget iPhone PIN
- 3. Unlock iPhone When Forgot Passcode
- 4. iPhone Lock Screen With Notification
- 5. Remove Passcode From iPhone
- 6. Unlock Found iPhone
- 7. Unlock iPhone without Computer
- 8. Unlock iPhone with Broken Screen
- 9. Unlock Disabled iPhone with iTunes
- 10. Unlock iPhone without Face ID
- 11. Unlock iPhone in Lost Mode
- 12. Unlock Disabled iPhone Without iTunes
- 13. Unlock iPhone Without Passcode
- 14. Unlock iFace ID While Wearing Mask
- 15. Lock Apps on iPhone
- 16. Bypass iPhone Passcode
- 17. Unlock Disabled iPhone Without PC
- 18. Unlock iPhone With/Without iTunes
- 19. Unlock iPhone 7/6 without PC
- 20. Unlock iPhone Passcode Screen
- 21. Reset iPhone Password
- 22. Bad ESN/Blacklisted IMEI on iPhone
- 23. Change Lock Screen Timer on iPhone
- 24. Remove Carrier Lock/SIM Restrictions
- 25. Get iMei Number on Locked iPhone
- 26. How to Check If iPhone is Carrier Locked
- 27. Check if an iPhone is Unlocked with iMei
- 28. Bypass iPhone Lock Screen Using Emergency Call
- 29. Change iPhone Screen Lock Time
- 30. Change Clock Font on iPhone To Fit Your Style
- Remove iCloud Lock
- 1. Remove iCloud from iPhone
- 2. Remove Activate Lock without Apple ID
- 3. Remove Activate Lock without Password
- 4. Unlock iCloud Locked iPhone
- 5. Crack iCloud-Locked iPhones to Sell
- 6. Jailbreak iCloud Locked iPhone
- 7. What To Do If You Bought A Locked iPhone?
- Unlock Apple ID
- 1. iPhone Asking for Apple ID Randomly
- 2. Get Apple ID Off without Password
- 3. Remove an Apple ID from iPhone
- 4. Remove Apple ID without Password
- 5. Reset the Security Questions
- 6.Change Credit Card on Apple Pay
- 7.Create an Apple Developer Account
- 8.Apple ID Verification Code
- 9.Change the Apple ID on MacBook
- 10.Remove Two Factor Authentication
- 11.Change Country on App Store
- 12.Change Apple ID Email Address
- 13.Create a New Apple ID Account
- 14.Change Apple ID on iPad
- 15.Change Your Apple ID Password
- 16.Apple ID Not Active
- Remove SIM Lock
- 1. Unlock iPhone Using Unlock Chip
- 2. Unlock iPhone for Free
- 3. Unlock iPhone Online
- 4. Unlock EE iPhone
- 5. Factory Unlock iPhone
- 6. SIM Unlock iPhone
- 7. Unlock AT&T iPhone
- 8. Unlock iPhone with IMEI Code
- 9. Unlock iPhone without SIM Card
- 10. Unlock Cricket iPhone
- 11. Unlock iPhone MetroPCS
- 12. Unlock iPhone with/without SIM Card
- 13. Unlock Telstra iPhone
- 14. Unlock T-Mobile iPhone
- 15. Unlock Verizon iPhone
- 16. iPhone IMEI Checker
- 17. Check If iPhone Is Unlocked
- 18. Verizon's Samsung Phones
- 19.Apple Watch and AT&T Deals
- 20.Add a Line to AT&T Plan
- 21.Unlock Your AT&T Phone
- 22.AT&T's International Plans
- 23.Unlock Vodafone Phone
- 24.Unlock Your TELUS Phone
- 25.Unlock Your AT&T Phone
- Unlock iPhone MDM
- 1. MDM On iPhone
- 2. Remove MDM from iPhone
- 3. Remote Management on iPhone
- 4. Unlock MDM Softwares
- 5. MDM VS MAM
- 6. Top MDM Bypass Tools
- 7.IoT Device Management
- 8.Unified Endpoint Management
- 9.Remote Monitoring Software
- 10.Enterprise Mobility Management
- 11.MDM Solutions for Device Management
- Unlock Screen Time Passcode
- 1. Reset Screen Time Passcode
- 2. Turn Off Screen Time without Passcode
- 3. Screen Time Passcode Not Working
- 4. Disable Parental Controls
- 5. Bypass Screen Time on iPhone Without Password
- Unlock Apple Watch
- ● Manage/transfer/recover data
- ● Unlock screen/activate/FRP lock
- ● Fix most iOS and Android issues
- Unlock Now Unlock Now Unlock Now




James Davis
staff Editor