Unified Endpoint Management: Simplify IT Management
Aug 16, 2024 • Filed to: Remove Screen Lock • Proven solutions
Unified Endpoint Management is common in organizations of all sizes, and for good reason. In a fast-paced digital landscape, the need for a comprehensive and streamlined approach to IT management has become imperative.
UEM has emerged as the answer to this pressing challenge. It offers a solution that empowers IT teams to manage, secure, and deploy corporate resources and applications across endpoint devices.
If you are curious to know more, this article explores the significance of UEM. We will shed light on its benefits and the role it plays in ensuring seamless technology integration.
Part 1: What Is Unified Endpoint Management (UEM)
Endpoint management is a crucial IT and cybersecurity process. It involves two main tasks: ensuring the right devices have access and applying security measures to prevent attacks.
Usually, a cross-functional team comprising network administrators and information security (infosec) experts oversees endpoint management. A good endpoint management server does the following things:
- Check if only the right devices can get into your network.
- Put special security software on the approved devices to keep them safe.
- Give the cybersecurity team a dashboard to watch over all the devices and what they're doing.
It would be best to use an endpoint management tool to keep your network and important stuff like company data, customer information, and secrets safe. In fact, personal devices, which you use at home and work, can be riskier than company-owned devices. That's because they might not have strong security. The way they connect to the network might not be very safe either.
Meanwhile, Unified Endpoint Management (UEM) empowers the infosec team to secure and control all endpoints through a centralized dashboard. Using the UEM dashboard, network administrators can:
- Update operating systems (OS) and applications on all relevant devices.
- Enforce security policies on registered devices.
- Remotely access devices for tasks like password resets or device wiping in case of loss or theft.
- Establish a process for employees to register their personal devices for network access.
Using UEM offers several advantages. First, it helps spot security threats and respond faster if there's a breach. UEM also makes updating devices with the latest software and security patches easy. Plus, it saves money by making things more efficient.

Part 2: What Are Endpoint Management Policies
Now, you might be curious about how UEM manages your data. Every organization should have clear endpoint management policies and enforce them by centrally controlling all connected devices.
An IT or a specialized DevSecOps team handles network security, including:
- Activating firewalls
- Using antivirus software
- Encrypting data
- Checking networked devices for weaknesses
An IT needs to oversee the entire technology setup. Then, it also ensures patches, updates, applications, and peripherals are properly maintained. Users should not have administrative control over their devices. They should follow best practices in endpoint management.
Even without admin control, individual users can introduce vulnerabilities. They can be through weak passwords, risky online behavior, and oversharing on social media. Hackers can exploit these vulnerabilities using social engineering tactics to breach the organization's networks and data.
You May Also Like:
4 Things You Must Know about Jailbreak Remove MDM
Part 3: Endpoint Management Example
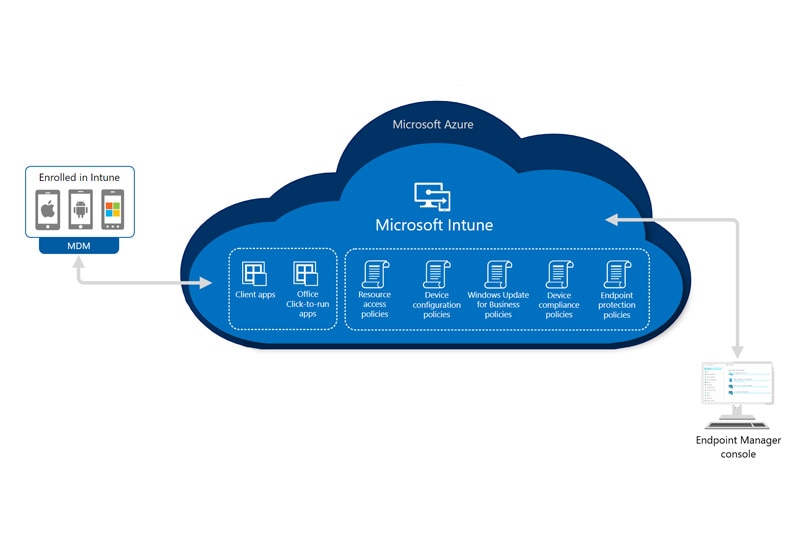
For the Endpoint Management example, Microsoft Endpoint Management Intune is a popular one. It's a comprehensive suite of products and services designed to provide a cloud-based UEM solution.
Microsoft Intune simplifies the management of various endpoints. They include those running different operating systems and spanning cloud, on-premises, mobile, desktop, and virtualized environments. It offers several key advantages:
- Data Protection
Intune enables data protection on company-owned and bring-your-own devices (BYOD) through non-intrusive mobile application management. It will ensure that sensitive company data remains secure, even on personal devices.
- Zero Trust Security
Intune empowers organizations to establish robust data protection and endpoint compliance measures that align with the Zero Trust security model. This means that security is enforced at every level of access.
- Enhanced IT Efficiency
Intune improves IT efficiency by bringing together device visibility, endpoint security, and data-driven insights, especially in hybrid work environments. Administrative tasks become more streamlined. End-user experiences are also enhanced.
- Integration Capabilities
Endpoint Manager Intune integrates with various services. They include Azure Active Directory (AD), on-premises Configuration Manager, mobile threat defense (MTD) apps and services, Win32 applications, custom Line-of-Business (LOB) apps, and more. This integration ensures a cohesive and adaptable UEM solution.
For organizations transitioning to the cloud or adopting more cloud-based services, Microsoft Intune endpoint manager can be a good starting point. It provides a robust and versatile UEM solution that can manage and secure diverse endpoints.
Part 4: What Are the Differences Between UEM, MDM, and EMM
In addition to UEM, two other terms are also often mentioned in IT management: Mobile Device Management (MDM) and Enterprise Mobility Management (EMM). While people sometimes use these terms interchangeably, it's crucial to recognize that each has distinct meanings within the information security community.
1) Unified Endpoint Management (UEM)
As discussed, UEM encompasses endpoint management software and associated tools that authenticate and regulate all types of endpoints. Endpoints refer to physical devices connecting with and exchanging data within a computer network. They can be computers, mobile devices, and emerging technologies.
So, UEM provides a centralized console for overseeing and managing all activities related to these endpoints. UEM ensures a unified and streamlined approach to IT management.
2) Enterprise Mobility Management (EMM)
Meanwhile, EMM centers around managing and monitoring mobile devices, including smartphones and tablets. But it also encompasses mobile infrastructure components like wireless networks, routers, and IoT (Internet of Things) devices. This comprehensive approach offers robust control and security measures for mobile and IoT endpoints.
3) Mobile Device Management (MDM)
MDM specifically pertains to the management and monitoring of mobile devices. It is particularly valuable for businesses and organizations. It allows them to control any computers they own and distribute them to their employees. MDM helps ensure the security of sensitive files and documents on these devices.
However, companies must remove the MDM profile first if they sell these devices. Otherwise, customers won't be able to use the device. They'll need to figure out how to get past it.
This is why the users might see a "Remote Management" prompt when using such devices. Many people buy iPhones or iPads with MDM profiles and then have to remove them to use the device.
How to Remove MDM on your iPhone/iPad:
To remove MDM on your devices, you can try using Dr. Fone's MDM Unlock feature. This process is user-friendly and requires no advanced technical skills.
Here are the steps:
Start by launching Wondershare Dr.Fone on your computer. Navigate to Toolbox > Screen Unlock > iOS.
Once you've entered the Unlock MDM iPhone function, pick the Remove MDM option.
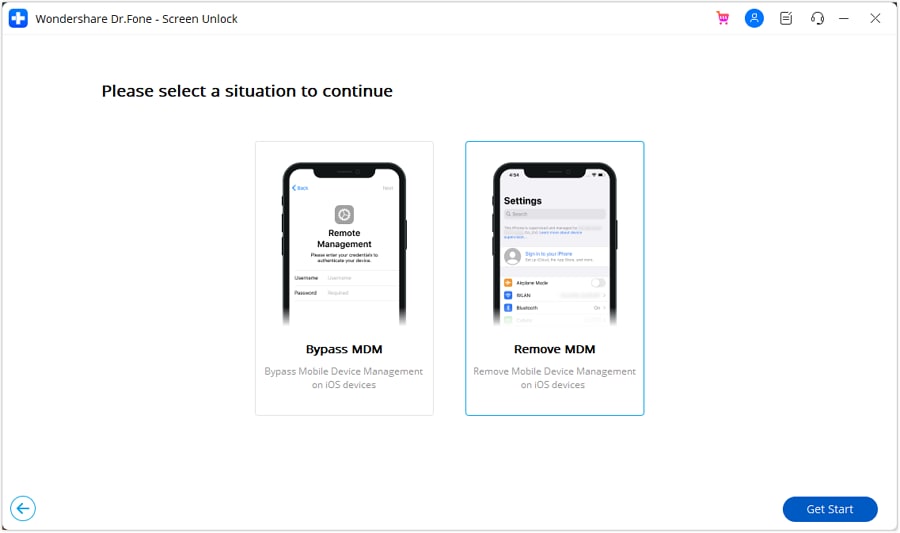
On the next screen, you'll find the option to remove the MDM lock from your iPhone. Begin the process by clicking "Start to Remove."
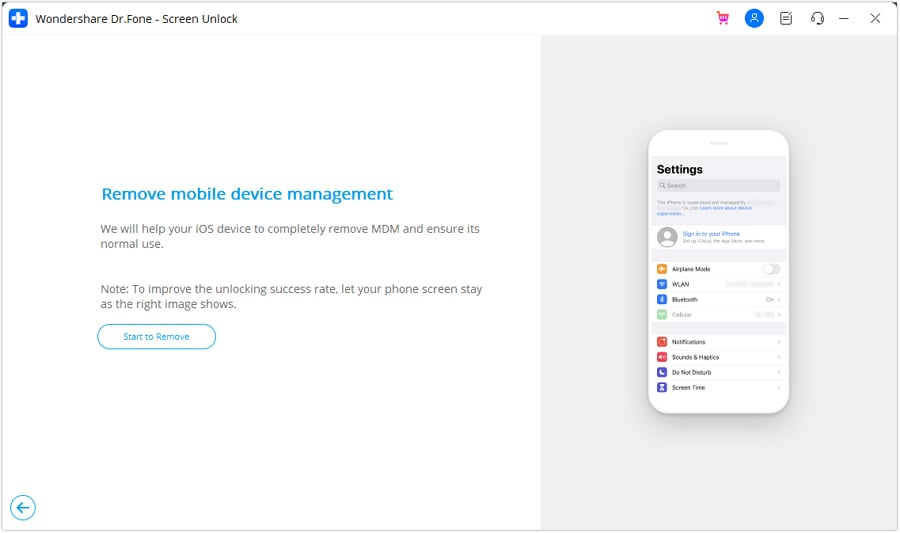
You'll encounter a prompt that asks you to disable the Find My feature. After disabling it, click "OK" on the screen to proceed with the removal.
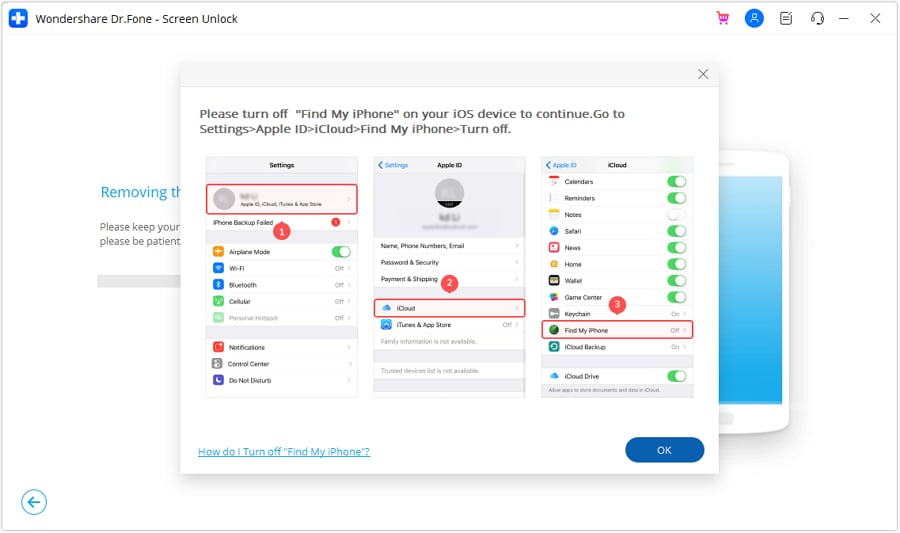
Keep an eye on the progress bar to track how far along the removal process has come.
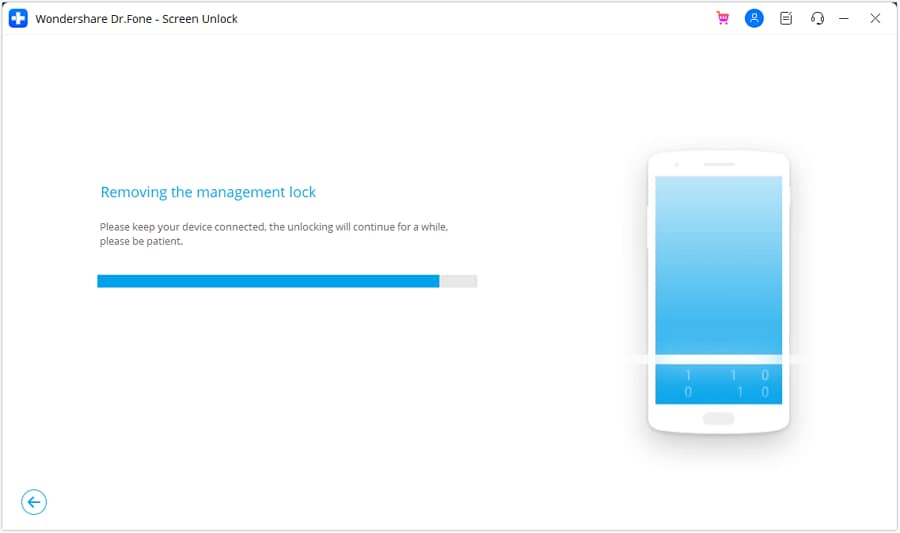
Once you have removed the lock, a message will appear on the next screen. Click "Done" to conclude the entire process of eliminating the local MDM.
Please note that after bypassing the MDM lock, the device may get locked again if it's reset or if its firmware is flashed. But, it's worth noting that this doesn't apply to devices locked with local MDM.
Conclusion
Unified Endpoint Management (UEM) is a crucial tool for modern organizations. It simplifies IT management by centralizing control over various devices. This tool also ensures security, and saving costs. UEM, like Microsoft Intune, protects both company and personal devices. It enhances data security.
While UEM, Mobile Device Management (MDM), and Enterprise Mobility Management (EMM) are related, each has its specific role. Embracing UEM is a strategic step towards ensuring a secure technology environment for businesses of all sizes.
iPhone Unlock
- Access Locked iPhone
- 1. Reset Locked iPhone Without iTunes
- 2. Erase Locked iPhone
- 3. Get Into Locked iPhone
- 4. Factory Reset Locked iPhone
- 5. Reset Locked iPhone
- 6. iPhone Is Disabled
- 7. Fix iPhone Unavailable Issue
- 8. Forgot Locked Notes Password
- 9. Unlock Total Wireless Phone
- 10. Review of doctorSIM Unlock
- iPhone Lock Screen
- 1. Unlock iPhone with Apple Watch
- 2. Unlock Forget iPhone PIN
- 3. Unlock iPhone When Forgot Passcode
- 4. iPhone Lock Screen With Notification
- 5. Remove Passcode From iPhone
- 6. Unlock Found iPhone
- 7. Unlock iPhone without Computer
- 8. Unlock iPhone with Broken Screen
- 9. Unlock Disabled iPhone with iTunes
- 10. Unlock iPhone without Face ID
- 11. Unlock iPhone in Lost Mode
- 12. Unlock Disabled iPhone Without iTunes
- 13. Unlock iPhone Without Passcode
- 14. Unlock iFace ID While Wearing Mask
- 15. Lock Apps on iPhone
- 16. Bypass iPhone Passcode
- 17. Unlock Disabled iPhone Without PC
- 18. Unlock iPhone With/Without iTunes
- 19. Unlock iPhone 7/6 without PC
- 20. Unlock iPhone Passcode Screen
- 21. Reset iPhone Password
- 22. Bad ESN/Blacklisted IMEI on iPhone
- 23. Change Lock Screen Timer on iPhone
- 24. Remove Carrier Lock/SIM Restrictions
- 25. Get iMei Number on Locked iPhone
- 26. How to Check If iPhone is Carrier Locked
- 27. Check if an iPhone is Unlocked with iMei
- 28. Bypass iPhone Lock Screen Using Emergency Call
- 29. Change iPhone Screen Lock Time
- 30. Change Clock Font on iPhone To Fit Your Style
- Remove iCloud Lock
- 1. Remove iCloud from iPhone
- 2. Remove Activate Lock without Apple ID
- 3. Remove Activate Lock without Password
- 4. Unlock iCloud Locked iPhone
- 5. Crack iCloud-Locked iPhones to Sell
- 6. Jailbreak iCloud Locked iPhone
- 7. What To Do If You Bought A Locked iPhone?
- Unlock Apple ID
- 1. iPhone Asking for Apple ID Randomly
- 2. Get Apple ID Off without Password
- 3. Remove an Apple ID from iPhone
- 4. Remove Apple ID without Password
- 5. Reset the Security Questions
- 6.Change Credit Card on Apple Pay
- 7.Create an Apple Developer Account
- 8.Apple ID Verification Code
- 9.Change the Apple ID on MacBook
- 10.Remove Two Factor Authentication
- 11.Change Country on App Store
- 12.Change Apple ID Email Address
- 13.Create a New Apple ID Account
- 14.Change Apple ID on iPad
- 15.Change Your Apple ID Password
- 16.Apple ID Not Active
- Remove SIM Lock
- 1. Unlock iPhone Using Unlock Chip
- 2. Unlock iPhone for Free
- 3. Unlock iPhone Online
- 4. Unlock EE iPhone
- 5. Factory Unlock iPhone
- 6. SIM Unlock iPhone
- 7. Unlock AT&T iPhone
- 8. Unlock iPhone with IMEI Code
- 9. Unlock iPhone without SIM Card
- 10. Unlock Cricket iPhone
- 11. Unlock iPhone MetroPCS
- 12. Unlock iPhone with/without SIM Card
- 13. Unlock Telstra iPhone
- 14. Unlock T-Mobile iPhone
- 15. Unlock Verizon iPhone
- 16. iPhone IMEI Checker
- 17. Check If iPhone Is Unlocked
- 18. Verizon's Samsung Phones
- 19.Apple Watch and AT&T Deals
- 20.Add a Line to AT&T Plan
- 21.Unlock Your AT&T Phone
- 22.AT&T's International Plans
- 23.Unlock Vodafone Phone
- 24.Unlock Your TELUS Phone
- 25.Unlock Your AT&T Phone
- Unlock iPhone MDM
- 1. MDM On iPhone
- 2. Remove MDM from iPhone
- 3. Remote Management on iPhone
- 4. Unlock MDM Softwares
- 5. MDM VS MAM
- 6. Top MDM Bypass Tools
- 7.IoT Device Management
- 8.Unified Endpoint Management
- 9.Remote Monitoring Software
- 10.Enterprise Mobility Management
- 11.MDM Solutions for Device Management
- Unlock Screen Time Passcode
- 1. Reset Screen Time Passcode
- 2. Turn Off Screen Time without Passcode
- 3. Screen Time Passcode Not Working
- 4. Disable Parental Controls
- 5. Bypass Screen Time on iPhone Without Password
- Unlock Apple Watch
- ● Manage/transfer/recover data
- ● Unlock screen/activate/FRP lock
- ● Fix most iOS and Android issues
- Unlock Now Unlock Now Unlock Now




Daisy Raines
staff Editor